The legend goes that the first computer crime took place in Lithuania at the end of the 1980s at “Sigma,” an association of factories that produced Soviet computer equipment. An engineer tweaked a rounding function in an accounting algorithm and transferred microscopic sums of money to a remote account. A confirmed first court case has been dated to 1992. An engineer at the Ignalina nuclear power plant coded and planted malware into “Titan,” the software system responsible for monitoring and managing the nuclear reactors.1 Between these two events, the Singing Revolutions took place and post-communist momentum commenced with its turmoil. The computer underground in the region emerged out of early BBS and FidoNet networking and opening markets, amid garage computer vendors, and internet cafes, university labs, and defunct industrial blocks.
This essay draws on personal observation, conversations, and public and private data archives from between 1995 and 2010, and the focus is one country, Lithuania. However, the experiences, I argue, may be familiar and recurrent throughout many other countries in the region. It is true that in many respects the computer undergrounds in post-communist Europe echoed or imitated the subcultural practices found elsewhere, such as in the US or Germany. But they also developed a distinct flavor steeped in the social transitions, network structures, geography, and languages specific to the region. Part of the generation growing up in the 1990s came of age in the computer underground and its peripheries. Thus, this is a coming-of-age-story as well as an overdue eulogy.
The economy of the 1990s was rough, and the post-revolutionary cultural scene became incredibly boring. Populated with Russian pop scene look-alikes, it encompassed no space for variety, for niche, for choice. Commodities like software and telecommunication services were expensive and rare, and so were books and lifestyle items. Curiosity and boredom were a frequent motive behind the initial impulse to start exploring technology: an intellectual activity rather than the development of a technical skill. Those who took that path also found different ways to overcome financial barriers. Some would use stolen credit card data to buy unaffordable books. Others would utilize phone line phreaking to access networks for free, an exercise in highly technical skills and a means to communicate with each other. Free and open source software expanded the possibilities of computing power to those who learned how to use it. While original commercial software was increasingly becoming more available, in many cases neither consumers, nor businesses, nor state institutions could afford it. Pirate software was traded under the counter, frequently by official software vendors themselves. Computers were slow, and so were networks. Thus, it made sense as a collective pastime to buy a case of beer and spend the night compiling operating system brains (also called kernels) or testing the boundaries of system security. The unlawful use of electronic data officially became a crime in 2003, and unauthorized access to computer systems in 2004, when the acts were introduced into the penal code.2 Throughout the 1990s when breaches were discovered, more often than not, the affected party used its own resources to invite the perpetrators for a talk in order to warn them off. Police intervention was theoretically possible, but under-the-counter settlements prevailed.
While the internet provided for many the first direct interactions with the global technoculture, the early post-communist internet communities in their daily life focused on the local. The imperative that “information wants to be free” was performed not just in spreading or copying information, but also in voluntary translations of seminal texts (predominantly from English and Russian) into local languages. Before Google Search and Google Translate, finding and translating counted as meaningful work within local communities. It served the direct purpose of sharing and increasing access to information, but also of claiming knowledge from other cultural contexts as one’s own and reconfiguring it to local mentalities. Original texts were also written and circulated, describing the technical details of local telecommunication networks, e.g. how to make free calls on specific public telephone models.
Also local at the time were the periodic moral panics about the internet in the mass media. A hacking website published a translation of The Terrorist's Handbook.3 A series of media articles followed, hyperbolizing the possible impacts and dangers for society, calling for censorship and blaming the authors for putting society at risk. One journalist perpetuated a hoax by impersonating a group of bombmakers that sold bombs from the handbook and bragged about it on an online forum. He then used it as a source of information for a newspaper article decrying the dangers of the internet. The Terrorist’s Handbook may have still resonated with memories of the very early 1990s when organized crime groups actually planted and detonated car bombs in a society otherwise far and free from the threat of terrorism (or a public understanding of it).
In the United States, authors such as Eric S. Raymond were vocal about establishing and maintaining a strict divide between ethical and unethical, legal and illegal, white hat and black hat approaches to computers and networks.4 In post-communist Europe, the divide was discussed as a philosophical issue, but the common stance was ambiguous at best, a matter of gray-hat drift. Some people and groups were more involved in shady dealings, others less so. Some were more egoistic and profit-minded, others less so. The same persons could work as a system administrator to protect networks and breach the security of neighboring networks in their free time.
The hyperlocal underground communities, sometimes comprised just of two or three people, operated in smaller towns. Larger groups, loosely organized in major cities, were still relatively small compared to the US or Germany. Groups focused on operation systems and network security coexisted with communities of crackers, specializing in the removal of software copyright protection, and carders, experts of credit card systems and their sometimes illegal use. Some of the members overlapped or were acquainted with at least a few people in other groups. Not everyone knew everyone, but everyone knew someone who knew someone else. Gossip spread quickly and inevitably. These small and loosely connected communities, where everyone may or may not have been a criminal, their shared secrets and rumors, grew into an implicitly trust-based coexistence. Friendships could break and virtual personas could hate each other, but what happened on the network, stayed on the network. These trust-based networks, in their own way, fostered curiosity, risk-taking, and legally ambivalent challenges.
The 15- to 30-year-olds that formed the core of the underground were the first cohort that grew up during the transition period or shortly thereafter, brought up by a generation of parents that took head-on the blows of social and economic upheaval. The era from 1990 to 2000 was marked by an early spike in divorce rates, steady growth of the unemployment rate, suicide, substance abuse, HIV deaths, and income inequality. Growing up for this generation – both within the underground circles and outside of them – resulted in a liberal attitude towards risk compared both to the previous generation and the one that followed. Coming out of communist-era hypocrisies, where everybody had to either comply with the party or stay silent in public, it became necessary to redefine what it means to have a personal identity and learn to use it socially. Especially in terms of identity-building, online communities provided ample opportunities for experiment. It was a tool which allowed for the discernment of the basic building blocks of personal identity like one’s name, visual style, knowledge, emotional expression, feedback and means of interaction, and then one could deconstruct and reconstruct the blocks in numerous ways, starting over as many times as needed.
Now largely irrelevant, the divide between offline and online was strong at the time. Network access was far from ubiquitous. Home internet access in the Baltics, for instance, was available to 2.3% of households in 2000, so being online was special. Both the physical and the virtual world were seminal in forming the personalities of the young women and men in and around the computer underground. They traded files physically – on floppy disks and later, on CDs and DVDs. They chatted online both in private one-on-one encounters and public channels. They organized and attended live events: technical meetups, political discussions, illegal raves, and punk gigs. It was inherently a social experience, using the network as much for technical exploration and skill-building, as for sifting through one's individual identity and socializing. These were not only networks of technical knowledge, but webs of tangible personal relationships. Curiosity about technology started the conversations, and friendships maintained them, traversing many non-technical topics.
The computer underground, as elsewhere around the world, was associated with a specific aesthetics, literary fiction, music, film, and architecture. “High-tech low life,” an essential definition of cyberpunk attributed to game creator Mike Pondsmith, had a specific meaning in the post-communist cultural milieu. Rather than a denial of mainstream consumerism, it was the essence of everyday life for many, a necessity rather than aesthetic or idealistic choice. “Apocalypse scheduled for tomorrow”5 seeped through communist-era housing blocks, a lack of public amenities, unstable incomes, emotional, and physical violence, and the grim climate, especially further North, as well as a myriad of survivalist tactics of disobeying the rules to make do for oneself or one’s closest friends. There was also a fertile crossover among the various technological groups and other youth subcultures. In musical scenes from punk to techno, do-it-yourself was the dominant ethos because commercial service providers neither existed nor could be afforded. Film consumers in the 1990s flocked to video rentals for pirate copies of VHS cassettes, dubbed in characteristic Russian voices that sounded as if the translator had their nose permanently pinched. Niche genres like cyberpunk and anime were available at some rentals due to owners’ curation, and places where the genres had earned a reputation, like the “Eliksyras” in Vilnius. Later, as more content became available online, film, and music consumption also relied on members of the community with permanent and much faster connections, like those working in internet cafes or who had access to the high-speed university link, Litnet. Digging, the (potentially illicit) exploration of industrial sites and abandoned buildings, was an authentic pastime. It was enabled largely due to post-communist deindustrialization, lots of abandoned sites near city centers, little ownership or social control over them, and the generational fatalism about risk.

Osiedle mieszkaniowe i opuszczony teren przemysłowy w Paneriai (WIlno), 2004. Zdjęcie: archiwum własne autorki.
The region was wedged between two major spheres of cultural influence: the English-speaking internet and its Russian counterpart, known colloquially as Runet. Before Russian faded out of the public education programs, both cultures had significantly shaped the intellectual sides of the post-communist computer underground. William Gibson and Neal Stephenson, on par with Sergei Lukyanenko and Mercy Shelly. Post-communism itself gave the world Christian As. Kirtchev, the Bulgarian known for the inspirational essay “The Cyberpunk Manifesto.”6 Elsewhere, Kirtchev said about the text, “It is written by an Eastern European in a former Soviet Bloc satellite country after the fall of communism. It is even given as a study at English class in a college to examine the ‘broken English.’ [sic]”7 The quote might serve to explain the niche of post-communist computer scene in a global context: a subaltern refusing to be silent, struggling with language and identity, while leveraging technical skills to gain an edge.
Kirtchev also wrote Chemical Illusions,8 a collection of short stories in English. The annotation reads: “[The stories in] Chemical Illusions are the latest black-market commodity on the street. They are fine strips of scripting code, designed to trigger chemical reactions within the logic chains of a recipient’s brain. Lies as real as the truth – an addictive experience which helps the desperate masses, living in a system of the not-so-distant future, to escape the absurdity of a harsh daily reality. The tales in this compilation were all written between 1997 and 2004 in Eastern Europe under the influence of an environment of apathetic misery lurking about former communistic concrete blocks and running over contemporary internet infrastructure laid on ancient cable grids.”9 The texts offer a mixture of narrative styles and cyberpunk visualizations that may seem crude in their literary value, but powerful for a different reason. They are eerily similar to the many literary attempts of others from the region, circulated as text files among friends, and never published. A noir commonality, a way of ruminating on everyday life, a way of writing not-quite-essays learned at the region’s secondary schools, yet another thread towards coming of age.

Egzemplarze dokładnie przyczytanych Chemical Illusions [Iluzji chemicznych], 2019. Zdjęcie: archiwum własne autorki.
The anti-authoritarian and anti-establishment ethos of computer undergrounds worldwide resonated strongly with post-communist anomie. In established (neo)liberal democracies, resistance to the state or “the system” was based on decades-old tensions and an intellectual tradition of critique towards neoliberalism, capitalism, and corporatism. In many respects, the American computer undergrounds took their cue from the counter-cultures of the 1960s and 1970s, inheriting modes of action like manifestos, political declarations, and a consensus towards supporting liberal values. Meanwhile, in post-communist space, recent history was precisely a struggle against the system – which *has been won* – and the disillusionment that followed. Many social practices and power relations of the Soviet era were inherited into the 1990s despite the nominal change of political systems, toning down the romantic notions of independence, freedom, and justice. Resisting the system, thus, was not so much a collective endeavor for social justice, but, rather, a personal revolt, and an act of identity establishment. An existential quest for meaning, rather than political individualism.
Online communities were an alternative to the hard civic society whose development at the time was funded by transnational civic society foundations. Although much of the politics was personal, there were also cases of public political activism. Two prominent proponents of the open source and free software movement have visited Lithuania to, among other things, give talks at the Parliament: Eric S. Raymond in 2002 and Richard Stallman in 2004. The trips were organized by “Open Source for Lithuania,” an organization lobbying for open source software in the public sector and public awareness of computer-related issues. The visits reflected a high point of political visibility and active attempts to shape public policies within the emerging discourse of information society. In 2005, a widely circulated petition against software patents was an example of going beyond national politics to discuss affairs on a wider European scale. An anti-ACTA10 rally was held in 2012 and became the last event that brought together the various internet communities from the previous era.
What happened? Eventually, the future that was longed for became the past that was missed. Mass internet consumption hit Lithuania in the 2000s: home internet access exploded from 2.5% in 2000; to 34.5% in 2006; and over 50% in 2009. For no particularly visible reason, the old internet fell silent. At first, people found they logged onto chat services and had less and less to talk about. Then, they stopped showing up. From 2000 to 2010 the optimism around Web 2.0 and user participation brought up a new generation of tech-savvy youth, intent on taking the previous generation’s ideals overground. Freedom of information resonated well with blogging, citizen journalism, and making friends on Twitter, Foursquare, or their local variations. Hackerspaces and startup accelerators started popping up, connecting the Baltics into with a network of increasingly uniform knowledge markets. Though different from the 1990s, it seemed all was set to be well, and the future was vibrant.
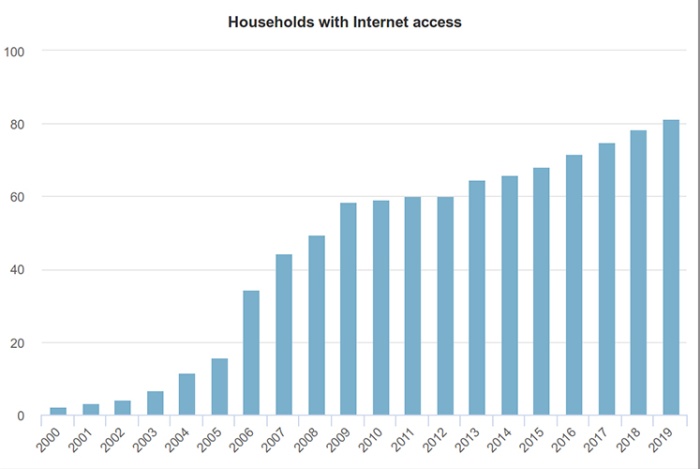
Wzrost dostępu do internetu w litewskich domostwach, 2000–2019. Źródło: Państwowy Depratament Statystyczny (2019). Gospodarstwa domowe z komputerami z dostępem do internetu. Portal statystyk urzędzowych. Online:https://osp.stat.gov.lt/.
However, after 2010, when information capitalism hit, user participation was replaced by data generation and information sharing was disrupted by content-serving algorithms. Most local web services did not survive the competition, and post-communist consumers became clients of the truly global internet industries along with the rest of the world. Ubiquitous Wi-Fi and smart devices upended the notion of the physical and the virtual as distinct spaces. Digital colonialism11 emerged at the time as a concept critiquing the shift of online power relations and emerging chasms between privacy, security, and secrecy, as corporate and state interests swept away individual self-determination.
Some of the most technologically skilled joined the rapidly expanding corporate workforce. Some switched to a different field altogether. Few chose to join organized cybercrime enterprises, which operate on principles mirroring the IT industry at large. It is the latter that may have sparked some of the claims by mass media as well as researchers, declaring that the post-communist states in Europe are home to the most sophisticated online criminals for hire.12 The risk-taking, trust, ethical ambiguity, and persistence of the 1990s generation may have contributed to the image. And while occasional lone hacker personalities like Guccifer or Popov13 may still show up in the media, the computer underground communities disbanded, and the edge has since moved on to other technologies like biotech or transportation. The epoch has dissolved into the fragility of memories, sentiment, and friendships: some maintained, some forever lost.
Acknowledgments
I would like to express my thanks to Juozas Valenčius for sharing research data he collected in 2012, which I have used to partially reconstruct the chronology of how the computer underground developed. Edgaras Leichteris has kindly agreed to a long late-night chat about the development of the internet in the 1990s and has shared his thesis on cybercrime, one of the first studies of the topic in Lithuania. Ieva Baršauskaitė helped me find the right scope for the topic and the appropriate words to talk about it. Almantas Karvelis supported me with nodal references, patterns, and suggestions, and pointed out the ironies of this endeavor.
I wrote this essay about the Lithuanian case, which I know best. If you had first-hand experience of the post-communist computer underground anywhere in the region and this text touches you, if you would like to agree or disagree, or share things that were significant to you personally and to the communities that you belonged to, please send me an email at maryja.supa@fsf.vu.lt.
BIO
Maryja Šupa, PhD, is a researcher at the Department of Criminology, Vilnius University, Lithuania. Maryja’s research interests include the theoretical and methodological problems in cybercrime research, algorithm ethics, and social control, and deviant aspects of emerging technologies. Her most recent research project focuses on tracing where niche technological countercultures moved after computers and networks hit mass consumption. Besides technology and crime, Maryja has also published academic articles about urban structures, cultural criminology, and online media.
Viktorija Rusinaitė, PhD, is a researcher, activist, and consultant interested in regime transition in the former Eastern Bloc. She is a co-founder of the research unit "Balticada" combining academic, journalistic, and artistic know-how to explore and analyze socio-political developments in the post-soviet sphere.
She is one of the organizers of Congress on Public Spaces in Vilnius and and co-creator of location-based demilitarization games in Šančiai, Kaunas, and Karoliniškės, Vilnius. Her recently defended PhD thesis on Belarusian Political Nomadism explores situations of inbetweeness experienced by traveling activists and organizations.
* Cover photo: The Terrorist's Handbook, Commodore 64 edition. Source: csdb.dk.
[1] Leichteris, Edgaras (1999). Kompiuterinės technikos panaudojimas kaip nusikaltimų padarymo būdas [The use of computer equipment for committing crimes]. Unpublished thesis. Vilnius: Vilnius University.
[2] The Penal Code of the Republic of Lithuania. Online (in Lithuanian): https://www.e-tar.lt/portal/lt/legalAct/TAR.2B866DFF7D43/TAIS_397523. English translation online: http://www.lithuanialaw.com/lithuanian-criminal-code-495
[3] Chaos Industries. The Terrorist’s Handbook. Online: http://www.dvc.org.uk/cygnet/tthb.pdf. Many versions and editions are floating around the web, from original text files, to HTML, to PDF.
[4] Raymond, Eric S. (2001). How to become a hacker. Online: http://www.catb.org/~esr/faqs/hacker-howto.html
[5] A sign-off signature from a chatlog. I am sure the quote has an original source, but it remained untraceable at the time of writing.
[6] Kirtchev, Christian As. (1997). “The Cyberpunk manifesto”. Online: http://project.cyberpunk.ru/idb/cyberpunk_manifesto.html; revised English translation online: https://www.neondystopia.com/cyberpunk-fashion-lifestyle/a-cyberpunk-manifesto-revised/.
[7] Wheeler, Isaac L. (Veritas) (2017). “ A Cyberpunk manifesto – revised”. Online: https://www.neondystopia.com/cyberpunk-fashion-lifestyle/a-cyberpunk-manifesto-revised/
[8] Kirtchev, Christian As. (2009). Chemical illusions: Anthology of cyberpunk tales from Eastern Europe. Lexington, KY: CreateSpace.
[9] Annotation on Amazon.com. Online: https://www.amazon.com/Chemical-Illusions-Anthology-Cyberpunk-Eastern/dp/144956402X/
[10] ACTA stands for Anti-Counterfeiting Trade Agreement, an international treaty to enforce intellectual property rights, signed in 2011, widely criticized, and currently not in force.
[11] I traced the term at least as far back as a thesis by 2005 where the term virtual colonialism was attributed to a book chapter by A. Kroker from 1996. See: Kent, Michael Ian Anthony (2005). The invisible empire: border protection on the electronic frontier. PhD thesis, Murdoch University, p. 313. Online: https://researchrepository.murdoch.edu.au/id/eprint/124/2/02Whole.pdf. The term went into wider usage with the rise and mass consumption of corporately owned global online services. For digital postcolonialism, see Jandric, Petar and Kuzmanic, Ana (2016). “Digital Postcolonialism”. In IADIS International Journal on WWW/Internet, 13(2), pp. 34–51. Online: https://bib.irb.hr/datoteka/794794.Jandric_Kuzmanic_journal.pdf
[12] See, for instance: Constantin, Lucian (2012). “Eastern European cybercriminals trump Asian counterparts, researchers say”. In Computerworld.com. Online: https://www.computerworld.com/article/2491491/eastern-european-cybercriminals-trump-asian-counterparts--researchers-say.html. For an industry overview, see: Gertz, Bill (2015). “The Global Cyber Crime Underground, Part 2: Russia and Eastern Europe”. In Looking Glass Cyber Threat Intelligence Blog. Online: https://www.lookingglasscyber.com/blog/the-global-cyber-crime-underground-russia-and-eastern-europe/. For an academic take, see: Kshetri, Nir (2013). “Cybercrimes in the Former Soviet Union and Central and Eastern Europe: current status and key drivers”. In Crime, Law and Social Change, vol. 60 (1), p. 39–65. Online reprint: https://libres.uncg.edu/ir/uncg/f/N_Kshetri_Cybercrimes_2013.pdf.
[13] For a compelling story about Popov, see: Poulsen, Kevin (2016). “The Ukrainian Hacker Who Became the FBI’s Best Weapon – And Worst Nightmare”. In Wired, May 2016. Online: https://www.wired.com/2016/05/maksym-igor-popov-fbi/